In a September 17 blog last year, TripleTree introduced our thinking on the healthcare information security exposures and hundreds of related data breach cases that were under review by the Department of Health and Human Services (HHS) and the SEC.
Our views (then and now) were that the complexities of healthcare data and the pace of innovation related to tools that securely manage it are facing clear and growing threats.
Earlier this month, health insurer Anthem was victimized in the industry’s largest data breach. While 80 million records were reportedly compromised at varying levels, less than half of those were Anthem members and the rest seem to have been exposed via Anthem’s business associate agreements which tie together dozens of Blues plans via a national BlueCard payment network.
As Anthem and outside investigators, including the FBI, piece together the facts, the thesis we promoted back in September is coming full circle as concerns mount that our increasingly digitized healthcare industry isn’t doing enough to thwart data attacks.
According to an Identity Theft Resource Center report, 2014 was a record year for data breaches in the U.S. (up 27.5% from 2013); with the healthcare industry emerging as the leading target of attacks for the third year in a row.
These trends coincide with the industry’s shift to value-based and distributed care models, which create exposures around broadened approaches for data collection and exchange across an increasingly connected continuum of care.
A Large Target Just Got Larger
In December, HHS proposed a new rule that would widen the amount of information shared as part of the Medicare Shared Savings Program (including ACOs) and “streamline access to such data to better support program and ACO function and goals…” As shown in Figure 1 below, this new rule includes not only the beneficiary’s name, date of birth, health insurance claim number and sex, but four other categories of information, including:
- Demographic data, such as enrollment status
- Health status information, such as risk profile and chronic condition subgroup
- Utilization rates of Medicare services
- Expenditure information related to utilization of services
Figure 1: What the Proposed Rule from HHS Means for Healthcare Data Exposure
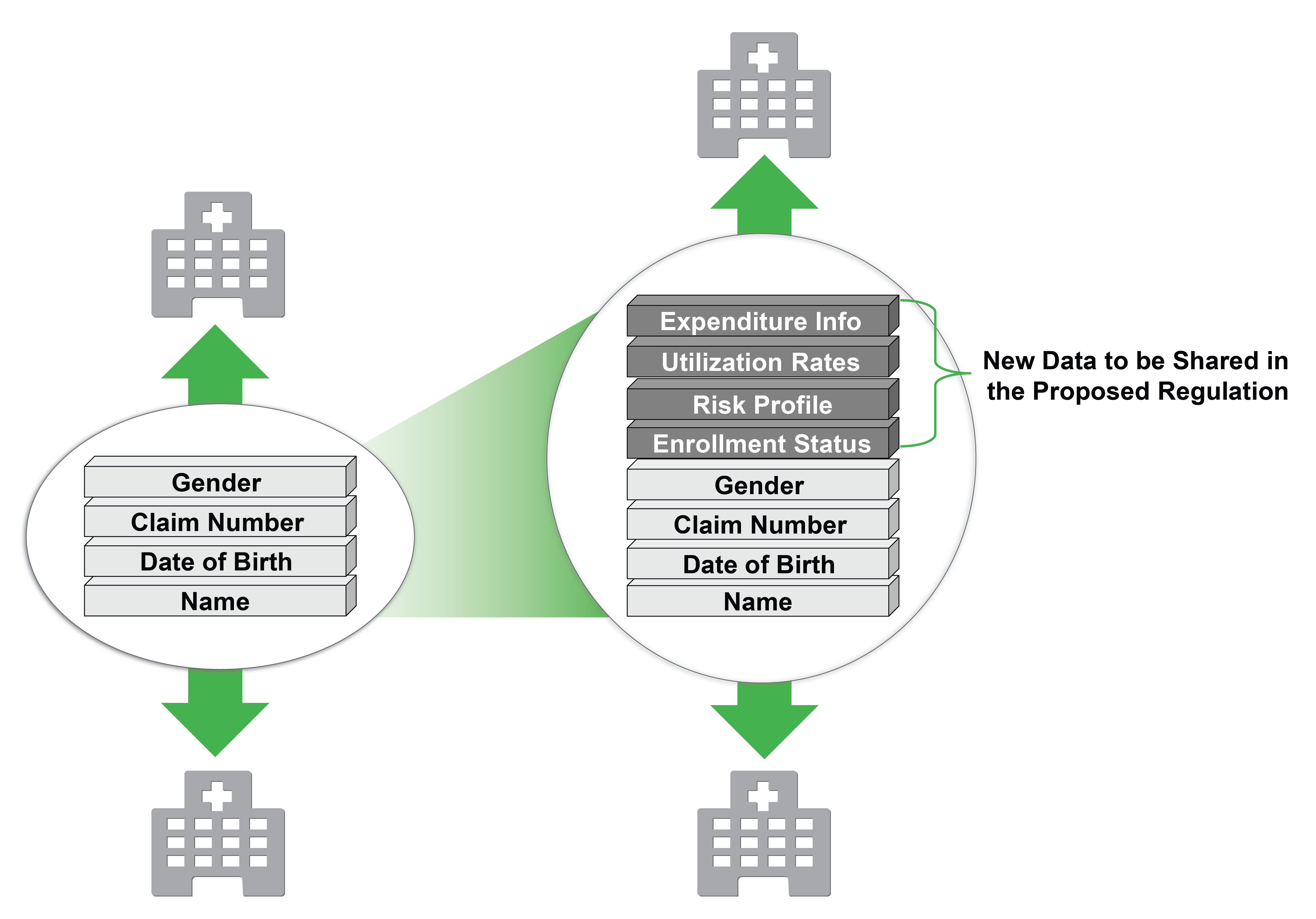
Source: TripleTree Analysis
New Vulnerabilities Are Emerging
In late December, a Minneapolis Star Tribune article discussed how Allina Health, a regional non-profit health system with 13 hospitals and 90 clinics, is joining other providers in partnering with the National Institute of Standards and Technology (NIST). The initiative is to study security vulnerabilities of wireless infusion pumps in hospital rooms, as they may provide criminals with access to a hospital’s network and other valuable information. Without proper protocols, connected devices and solutions could add to the rapidly growing list of potential data entry points for criminals. When combined with the increased amount of information being collected and shared, these new vulnerabilities create the perfect storm for hackers seeking valuable healthcare data.
Industry Regulators and Other Healthcare Stakeholders Take Action
- In 2015, the HHS Office for Civil Rights (OCR) is expected to begin a random audit program not only of covered entities, but also business associates – expanding their focus from providers to the broader healthcare landscape
- The Financial Services Department of New York announced it will introduce stringent cybersecurity standards and will begin performing targeted assessments and reviews of insurance companies (which will likely impact healthcare payers)
- The National Health Information Sharing & Analysis Center (NH-ISAC) and Center for Internet Security (CIS) announced a partnership to improve and strengthen nationwide cybersecurity measures for the healthcare industry, including a focus on medical devices
Stand alone, these measures will not be sufficient to combat this criminal threat, but are the beginnings of an alignment between regulatory and technology-based solutions that will mature over time.
Do these levels of disruption represent the ‘new normal’ in healthcare data security? We’ll be keenly watching this sector given the obvious opportunities for security-minded healthcare vendors (or data security leaders from other industries) to bring relevant thinking and data protection solutions to sector stakeholders in 2015 and beyond.
Let us know what you think.